Analysis as the essential part of the incident response process in a post-pandemic era
The pandemic has forever changed our lives, and the global workforce.
Restrictions and “stay at home” lockdowns imposed by governments around the world forced many organisations to pivot—virtually overnight—to support an exclusively or predominantly remote workforce.
The result of the dramatic shift to remote working was that very few were prepared to support their employees with a secure environment for them to effectively do their jobs while at home.
Swissinfo.ch reported that in Switzerland the number of cyberattacks reported to the Swiss National Cyber Security Centre (NSCC) was three times higher than its average in April of 2020. This included incidents of phishing, fraudulent websites, and other forms of direct attacks on private sector organisations.
THE INTENSIFYING CYBERSECURITY THREAT LANDSCAPE
The increased cyberattacks on organisations can be attributed to a rapidly intensifying cyberthreat landscape. In an article published by Deloitte, Impact of COVID-19 on Cybersecurity, they suggest that some of the factors contributing to a more dangerous cyberthreat landscape include:
- Employees with less supervision and fewer technical controls may be tempted to commit fraud, IP theft, or other forms of malicious insider threat activities
- Data security measures in place were not—and still may not be—fit or robust enough to handle a sudden shift to remote work making corporate networks vulnerable
While both of these factors present real and serious potential harm to an organisation, with an effective Incident Response plan and tools in place, the risk that they pose can minimised.
Cynet provides a succinct definition of Incident Response:
Incident response (IR) is a set of policies and procedures that you can use to identify, contain, and eliminate cyberattacks. The goal of incident response is to enable an organization to quickly detect and halt attacks, minimizing damage and preventing future attacks of the same type.
An effective IR plan generally has four phases each of which are comprised of several activities and likewise their own set of tools.
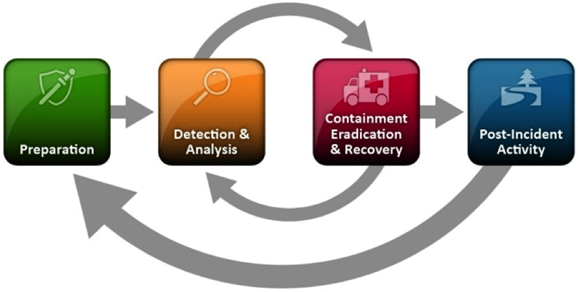
Unfortunately in today’s cyberthreat landscape for many organisations it’s not a matter of if a cybersecurity incident, but rather when a cybersecurity incident will occur. Therefore regardless of how prepared an organisation may be, they will still need to the tools in place to—not only detect but also—analyse incidents.
As a result: arguably one of the most important phases of this lifecycle is the analysis phase of the process. In this phase specialised digital forensics tools, such as Magnet AXIOM Cyber, play a key role in discovering and validating the root cause or indicators of compromise of a security incident such as a malware attack or an insider threat attack like IP theft.
THE RISE OF THE HYBRID MODEL OF WORK
In the post-pandemic era, a hybrid model of work will emerge: one that combines some remote work with working from an office. McKinsey suggests that in the US, 22% of employees will be able to work remotely between three and five days a week. Now more than ever before, it’s imperative that organisations have the tools at their disposal to effectively and reliable collect data for the purposes of a digital forensics investigation from endpoints that are not connected to the corporate network.
And it’s not only computer endpoints that represent sources of data for investigations. Data that is crucial to providing a complete picture of an entire security incident, for example IP theft, resides on mobile devices as well as in the cloud.
In Magnet Forensics’ 2021 State of Corporate Digital Forensics in Cybersecurity Report, they found that the top four sources of data for their investigations were mobile devices, computers, remote endpoints, and cloud evidence.
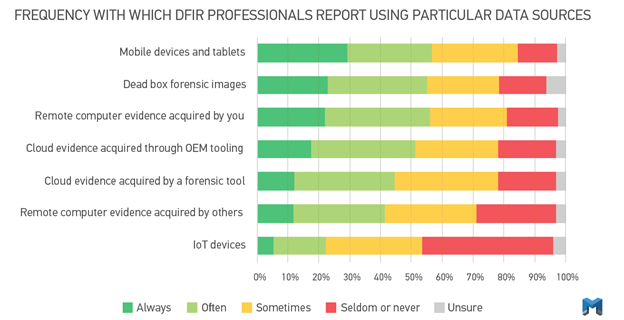
To ensure the analysis phase of the IR process is successful and thorough, tools that can acquire from computers (including Mac, Windows, and Linux), mobile devices, and cloud sources must be employed.
Without the proper digital forensics tools, the Incident Response process breaks down and companies are left vulnerable and exposed to malicious attacks from bad actors both internally and externally. The results of the intensified cybersecurity threat landscape and lack the proper tools to combat it are not only monetary, they extend into customer trust, and brand reputation which can often be irreparable. While some organisations may have the ability to weather that storm, many do not and unable to recover at all.
To learn more about how you can arm your organisation with Magnet AXIOM Cyber, a digital forensics solution with the capability to collect and analyse data from computers—including remote endpoints not connected to the corporate network—mobile devices, and cloud sources, visit magnetaxiomcyber.com.





