Cyber Security Challenges Affecting The Utilities Sector
Sad, but seemingly enduringly true, cyber security breaches and attacks remain a pervasive threat in 2024. Indeed, according to the government’s cyber security breaches survey 2024, half of businesses (50%) and around a third of charities (32%) report having experienced some form of cyber security breach or attack in the last 12 months – and this figure grows ever higher for medium businesses (70%) and large businesses (74%).
Moreover, in November last year, the National Cyber Security Centre (NCSC) warned about an ‘enduring and significant’ threat of a cyber attack upon the UK’s Critical National Infrastructure (CNI). This includes threats to utility organisations such as water and waste utilities, electricity and gas providers, and transport and telecommunications companies, as well as threats to the operational technology (OT) that controls and monitors these industrial systems.
Remember, cyber attacks against OT systems and critical infrastructure are ranked among the top five most significant risks by the World Economic Forum, and the NCSC’s warning arises against a worrying backdrop of rising international and geopolitical tensions (with an increasing number of utility-aimed cyber attacks already occurring overseas).
Why do cyber criminals target utility organisations?
Along with 2024’s geopolitical risks (e.g., tensions between Russia and NATO, strategic competition between the US and China, and even political instability within the UK itself), whereby hostile intelligence services would look to cause catastrophic, disruptive consequences to the UK’s public health and safety (not to mention our economy), there are several reasons why utility organisations make an attractive target for malicious actors. Key security drivers include:
Legacy system vulnerabilities
A lot of the utility sector’s legacy infrastructure was built to provide services to the UK; it was not built with security-by-design, as is the case with a lot of new infrastructure, thankfully. Aging infrastructure combined with the cost and operational difficulties involved in shutting down vital utility OT for maintenance and upgrades, unfortunately, makes CNI and utility organisations especially vulnerable to cyber attacks.
More competent threat actors
Sadly, cyber criminals are more competent than ever, a combined consequence of technology advances (having access to increasingly sophisticated tools and techniques for carrying out attacks, e.g., advanced malware, exploit kits, and hacking frameworks); greater connectivity (the increasing interconnectedness of devices and systems, often referred to as the Internet of Things (IoT), provides cyber criminals with more potential targets and avenues for attack. This is particularly true for the utility sector when we consider the use of smart meters, the integration of IT and OT, and the increasingly remote monitoring and control of systems); and cybercrime-as-a-service (CaaS platforms allow for less skilled individuals to launch sophisticated cyber attacks by offering a range of malicious services such as botnet rentals, ransomware-as-a-service, and distributed denial-of-service (DDoS) attacks for purchase).
Complex regulatory demands
The ever changing regulatory and legal landscape utility organisations contend with make it difficult for the sector to maintain regulatory compliance. This, along with networks and obscure connection points that can be difficult to monitor, and their large, often sprawling, supply chains, leaves utility organisations open to both data breaches and the potential fines that go along with failing to meet regulatory demands.
Talent shortages
The utility sector continues to struggle with having enough resource to build sufficiently robust security systems, a concern that is linked to the disparity between the demand for skilled cyber security professionals and the available talent pool with the requisite expertise (oh, and a lack of industry-specific training programs to boot). This skills gap poses significant challenges for utilities in effectively defending their critical infrastructure against cyber threats, particularly when we consider the rapidly evolving threat landscape (which requires constant training and updates for cyber employees) and the complexity of utility organisations’ infrastructure, which requires specialised knowledge and skills.
Is AI helping to drive cyber attacks on the utility sector?
Although artificial intelligence (AI) has been around for a while, with origins dating back to the mid-20th century, its rising popularity – driven by advancements in computing power, data availability, and algorithmic innovation – means it plays an increasingly significant role in cyber attacks across various sectors, and this includes utilities.
While we can’t blame AI for the security vulnerabilities surrounding utility companies, the problem is that malicious threat actors can leverage AI-powered tools and techniques to enhance the effectiveness, speed, and sophistication of their attacks. This might impact the utility sector in the following ways:
Automated threat detection and response
AI-powered systems can be leveraged to enhance the offensive capability of threat actors by enabling them to access powerful malicious code and TTPs (tactics, techniques and procedures) without the requirement of in-depth technical knowledge themselves. This means cyber criminals can launch more targeted and adaptive attacks against utilities’ infrastructure.
Advanced malware
Algorithms can analyse vast amounts of data to create customised and evasive malware variants capable of bypassing traditional security measures. These advanced malware strains can infect utilities’ systems, disrupt operations, and potentially cause widespread damage.
Targeted spear phishing
AI-driven spear phishing attacks use machine learning algorithms to craft highly personalised and convincing phishing emails that trick employees into divulging sensitive information or clicking on malicious links. Utilities’ employees may inadvertently fall victim to these sophisticated social engineering tactics, leading to security breaches.
Adversarial machine learning
Cyber criminals are exploring adversarial machine learning techniques capable of subverting security systems deployed by utilities, even those with AI capabilities themselves. By exploiting vulnerabilities in AI algorithms, attackers can evade detection whilst infiltrating utilities’ networks.
IoT botnets
AI algorithms can be used to create and manage botnets comprising Internet of Things (IoT) devices. These botnets can launch distributed denial-of-service (DDoS) attacks against utility companies’ infrastructure, disrupting services and causing operational disruptions.
Data poisoning and manipulation
AI-powered attacks can target utilities’ data infrastructure by poisoning training data used in AI models or manipulating data to deceive AI-based security systems. This can lead to false positives or negatives in threat detection, undermining the effectiveness of the organisation’s cyber security defences.
Predictive cyber-attacks
AI algorithms can analyse historical attack data to predict future cyber threats and plan pre-emptive attacks against infrastructure. By exploiting weaknesses in utilities’ security stance, threat actors can launch coordinated and strategic attacks with greater precision and impact.
How can we mitigate future risk?
To help the utility sector – and IT/OT environments in general – to bolster their security practices, I recommend a three-tiered approach:
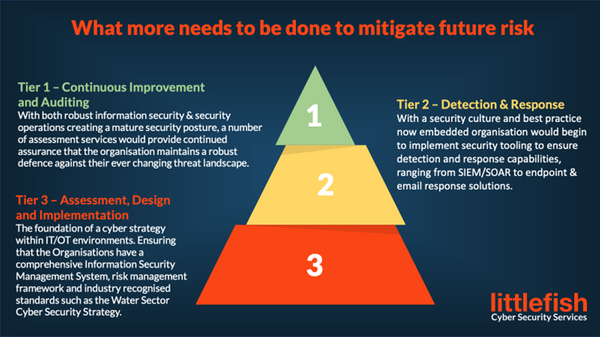
Tier three: beginning with a strong foundation
It’s important to begin with a core assessment, design, and implementation phase. This will establish alignment of the current utilities environment against industry best practice standards and include an evaluation of risk, vulnerabilities, and the organisation’s threat landscape.
The design phase will carefully consider design elements and associated documentation, e.g., network zoning/segmentation, vendor and supply chain security, and attack surface minimisation through areas such as secure remote access and enforcement of a defence in-depth strategy.
With a comprehensive design in place, changes are then implemented into the network ensuring that key areas such as interoperability, along with compatibility and maintenance of the systems used, are considered.
Tier two: building and embedding a true security culture
Not just referring to the systems themselves, it’s important to ensure that end users in the utility sector understand and have been trained in cyber security best practices (and that this training is regularly refreshed to keep security a top priority).
The environment will also require reactive security tooling to ensure that utilities organisations have robust detection and response capabilities along with the required end-to-end resources to keep these capabilities up-to-date (e.g., ensuring that detection rules are tuned, that tooling is up to date with the latest tactics, techniques and procedures (TTPs), that automation is leveraged to its fullest extent, and so on).
These capabilities allow for a dedicated security team to ensure that threats to the OT environment maintain a reduced dwell time and the team to contain and eradicate any threats.
Tier one: topping with constant improvement
With tier two being a continuous process, it’s important that utilities companies don’t take their foot off the pedal and become complacent.
To this end, making sure that internal audits are carried out, and that security procedures and technology are evaluated regularly, provides utilities organisations with the knowledge they need to continually improve and adapt their security strategy.









